IUID Vendor User Roles
IUID includes the following Vendor User Roles:
1. IUID Vendor Role
2. IUID Vendor Group Administrator (GAM) Role
Vendor
A vendor is a provider of goods and/or services to the government. It is a role used by vendors, suppliers, and contractors.
The Vendor uses IUID to:
- - Register for access to the IUID Registry for IUID Registry access.
- - Match the validated DUNS or CAGE codes that the vendor is registered for by using the view-only capability of IUID Data.
- - Add IUIDs and correct and update previously entered IUIDs.
- - Run reports and queries against data that match the validated DUNS or CAGE codes that the vendor is registered for.
Return to the TOP of the page
Vendor Group Administrator (GAM) Role
GAM: The users of IUID are broken down into groups on seven levels. Each group is administered by one or more Group Administrators (GAM).
Group Structure In IUID
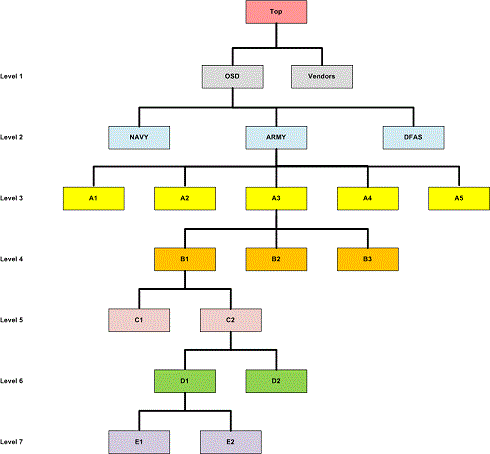
The graphic provides a depiction of the general IUID Group Structure. It portrays the IUID Group Structure 7 levels deep.
Tiered Jurisdiction
- - The GAM can edit user profile information for two levels: their own level and the level below their level.
- - The GAM has view-only access to user information for all other levels below their current level.
Group Levels In IUID
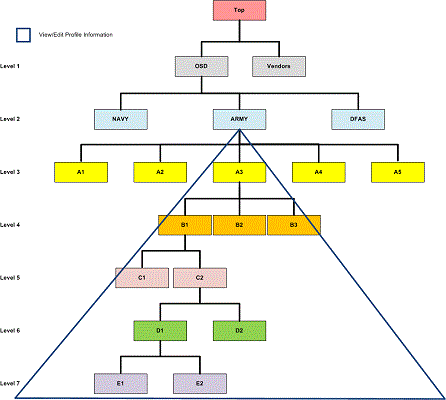
The graphic provides a depiction of the general IUID Group Level Structure. It portrays what user profiles the GAM can edit, and what user profiles the GAM can view.
Multiple Roles
Typically, a GAM is appointed from among security-type individuals in an organization, but a GAM can also have the role of Contractor (Vendor), Inquiry, or Legacy Submitter depending upon organizational business practices.
The GAM has eight major administrative abilities in IUID:
- - Manage Group Structure
- - Administer Location Codes
- - Look up group names and GAM information
- - View and edit User Profile Information
- - Activate (add) and deactivate users
- - Use Activation Reports
- - Reset user passwords
- - Reset certificates
Return to the TOP of the page
 7.6.3.1
7.6.3.1
 7.6.3.1
7.6.3.1
 7.6.3.1
7.6.3.1